Conflict in the Cyber Age
Why the world must act to end the cyber arms race
Chris Philpot illustration for Foreign Policy
Cyberattacks have occurred for decades, but the Stuxnet incident marked a pivotal moment in cybersecurity. Stuxnet, a cyber operation that targeted gas centrifuges used in Iran’s uranium enrichment program in Natanz, launched a global cyber arms race when it became public in 2010. While its impact was primarily contained to Iran’s nuclear facility, the high-profile attack demonstrated how nations can weaponize cyber tools to wreak havoc not only on computers and servers, but on critical infrastructure and government facilities to achieve foreign policy objectives. Since then, malicious actors have used and modified the Stuxnet code to attack a range of targets, including water treatment plants, power plants and gas lines. Although no one has claimed responsibility for Stuxnet, it possesses the signature of a state operation with cybersecurity experts linking its origin to US and Israeli intelligence.
Two years after Iran learned of Stuxnet, it initiated its own cyberattacks, first against the world’s largest oil company Saudi Aramco, in which hackers destroyed data on 30,000 computers, and later on American banks, causing millions of dollars in lost business. By 2014, North Korea joined in the cyber arms race with a hack into Sony Pictures that caused as much as $35 million in damages. Amid these attacks, then-US Defense Secretary Leon Panetta sounded the alarm over the potential for a “cyber Pearl Harbor” on critical infrastructure.
As threats to governments and private industry spread across borders, the UN’s Group of Governmental Experts (GGE) on Information Security called in 2013 and 2015 for the application of international law in cyberspace, including voluntary norms of responsible state behavior, state sovereignty, and the protection of human rights and fundamental freedoms, to which all members of the UN General Assembly agreed. In 2016, the North Atlantic Treaty Organization (NATO) similarly recognized the growing risks to international security, identified cyberspace as an operational domain and expressed the need for member states to bolster their cyber defense of national infrastructure.
To date, however, these efforts have demonstrably failed to deter attacks, hold bad actors accountable or sufficiently protect citizens. Rapidly evolving cyber capabilities, declining costs and relatively low barriers to entry have made the digital weapons increasingly accessible and powerful tools, and a force-equalizer among state and non-state actors. While essential for 21st-century economies, the proliferation and integration information and communication technologies (ICT) further expands the attack surface, requiring more agile and sophisticated defenses.
The Rise of State-Sponsored Hacking
Cyberspace is now a strategic domain as states use cyber tactics to conduct stealth attacks on rivals and target private industry for espionage and commercial gain, helping to level the geopolitical playing field. For state actors, the cyber domain is fast becoming the weapon of choice and is a “short of war” means to pressure other governments, manage conflict, impose costs on leaders and project national power. Over the last few years, the rate and sophistication of cyber incidents has increased sharply. According to a recent study by HP, from 2017 to 2020 the frequency of state-sponsored cyberattacks doubled, with an average of 10 publicly attributed cyberattacks per month in 2020. Threat actors’ techniques have also advanced, making them harder to identify and more threatening to targets.
According to Microsoft’s Digital Defense Report 2020, cyberattacks are becoming more sophisticated with state-sponsored actors employing new reconnaissance techniques to increase their chances of compromising high-value targets through credential harvesting, malware, and Virtual Private Network (VPN) exploits.
While the types of operations have varied, they have increasingly taken the form of mis- and disinformation campaigns. The Oxford Internet Institute found that in 2020, organized disinformation campaigns were waged in 81 countries, and government agencies in 62 countries used computational propaganda to shape public attitudes. States’ growing use of ICT-enabled covert information campaigns that seek to influence the overall stability of other states is raising concerns about their threat to the international community. These campaigns already permeate society and institutions, and we are only beginning to discern the breadth of damage and costs.
While mis- and disinformation attacks are on the rise, the preponderance of known state-sponsored cyberattacks involve data extortion through the use of ransomware, intellectual property (IP) theft and surveillance. As the boundary between the physical and digital world shrinks, such politically motivated cyberattacks can inflict widespread damage and tremendous direct and indirect costs—with consequences that transcend borders. In the past year alone, intelligence-gathering attacks to acquire vaccine-related IP have been linked to China, Russia and North Korea; Chinese state-sponsored surveillance operations and espionage efforts targeted pro-democracy organizations and individuals in Hong Kong; and unattributed ransomware attacks spread across more than 400 hospital and healthcare facilities in Puerto Rico, the United Kingdom, and the United States, causing an estimated $67 million in damages. While such attacks are a global issue, the US is the most targeted country for nation-state activities, followed by the UK, Canada, South Korea, and Saudi Arabia, according to Microsoft’s 2020 Digital Defense Report.
Perhaps as worrisome as the attacks themselves is their frequent and increasing use during peacetime, when rules of engagement and international humanitarian law do not clearly apply. As cyber defenses of high-value targets have improved, threat actors have turned to supply chain attacks in which they compromise a supplier’s software or hardware prior to installation in order to infiltrate data and manipulate IT hardware, operating systems, or services. In 2019, supply chain attacks increased by 78 percent. According to HP, at least 27 supply chain attacks associated with state-sponsored actors occurred between 2017 and 2020. The rapid digitalization of industry and services, and growing reliance on digital infrastructure, particularly during the pandemic, have experts anticipating further escalation of such attacks across cyberspace.
State actors also conduct cyberattacks targeting physical infrastructure during or in response to kinetic conflicts. This blend of conventional and non-conventional methods of warfare is known as “hybrid warfare.” In a 2020 study, 40 percent of analyzed state-sponsored incidents involved a cyberattack on assets that have both physical and digital components, such as power plants, waste water systems and running dams. Such strategies are invaluable to state actors’ efforts to advance their broader regional and geo-strategic policy goals, as demonstrated by the destructive attacks by Russian-backed hackers that sabotaged critical infrastructure in Estonia, Georgia, and, most dramatically, Ukraine, where in 2015 a quarter-million Ukrainians lost power after a cyberattack.
Global State-Sponsored Cyberattacks
Since 2005, 35 countries are suspected of sponsoring 510 cyber operations with China, Russia, Iran, North Korea and the United States engaged in the majority of the cyber activity. Of 121 operations in 2020, more than 77 percent were acts of espionage.
Note: This map was adapted from the Council on Foreign Relation’s (CFR) Cyber Operations Tracker to include a breakdown and description of the most common types of cyberattacks by specific countries and examples of cyber operations and their associated costs. All instances of publicly known state-sponsored cyber activity are collected from open-source information and existing repositories of state-sponsored incidents, such as CFR, Florian Roth’s APT Groups and Operations, the Center for Strategic and International Studies’ (CSIS) list of significant cyber events, and Kaspersky Lab’s Target Cyberattacks Logbook. The data exclusively tracks incidents and threat actors engaged with denial-of-service, espionage, defacement, destruction of data, sabotage and doxing.
Source: Council on Foreign Relations. (n.d.). Cyber Operations Tracker. Retrieved July 13, 2021, from https://microsites-live-backend.cfr.org/cyber-operations#OurMethodology
Cooperation Between State-Sponsored Attackers and Cybercriminals Elevates Security Risks
The cyber weapons used by state actors vary in sophistication and scope, with half of cyberattacks involving low-budget tools. More complex cyber weapons and operations can be resource-intensive and require vast domain and server infrastructure, as well as talented hackers on hand. For instance, threat actors may seek an unknown vulnerability in software – a zero-day exploit – in order to penetrate a system, especially one not connected to the internet. Such an operation can be expensive, with documented prices for a zero-day exploit ranging from $60,000 to $2.5 million, with no guarantee that the exploit will work. As a result, some state-sponsored attackers are leveraging the cybercrime market and collaborating with cybercriminals to fund and support their cyber operations.
The costs of these attacks to the victims and to society are growing exponentially. In 2021, Colonial Pipeline, an American oil pipeline system that originates in Houston, Texas and carries gasoline and jet fuel to the southeastern United States, suffered a ransomware attack that resulted in a $4.44 million payoff ($2.3 million was later recovered), drastically raised gas prices, and necessitated restoration work costing tens of millions of dollars. Weeks later, JBS Foods, the world’s largest meat company by sales, also paid $11 million in response to a ransomware attack by a Russian-linked cybercriminal group that forced nine plants to shut down in Australia, Canada, and the US. Experts fear that the disruption, which put immense pressure on an already strained global food-supply chain, may inflate beef prices for the next two to three years. By 2025, cybercrime is anticipated to cost the global economy $10.5 trillion per year (or $20 million per minute), greater than the current nominal GDP of Japan and Germany combined.
Despite the high cost of such attacks, some governments remain unwilling or unable to prosecute these types of crimes, allowing many cybercriminals to continue their ransomware attacks with impunity. The US Ransomware Task Force called ransomware a “national security risk that threatens schools, hospitals, businesses and governments across the globe.” Proceeds from ransomware attacks can help fund state-sponsored objectives, such as developing a nuclear weapons program or evading economic sanctions. This was illustrated by a 2016 incident in which North Korean state-sponsored hackers attempted to steal at least $1 billion from financial institutions around the world and successfully ran off with $81 million from Bangladesh’s central bank. Such risks are compounding as threat actors learn from one another and replicate tactics and tools employed by advanced state and non-state actors alike. In some instances, governments have shared hacking tools with cybercriminals and have purchased custom-made weapons, such as targeted malware or software exploits, through the dark web and other covert sources, in addition to stockpiling zero-day exploits. The emergence of sophisticated “cybercrime-as-a-service” schemes have afforded anonymity to state actors that seek to mask their efforts behind third-party contracts, thereby establishing “an almost impenetrable wall of plausible deniability.”
As the ease of conducting cyber operations grows, and more actors navigate the cyber arena, hacks by smaller, loosely affiliated, and ideologically motivated groups are also emerging as security threats. Recent examples include the ransomware hacks against French hospitals, the attempts to change the chemical levels in a Florida water-treatment facility, and the attack on the Massachusetts Steamship Authority this past year. Although the occurrences of cyber incidents around the globe can appear isolated from one another, the capabilities and impacts transcend borders.
Cyber Incidents by Top State-Sponsors
The following countries were chosen based on the total number of cyber operations they have reportedly sponsored, according to the CFR Cyber Operations Tracker. The examples referenced were chosen based on publicly available information regarding the cost of an attack by a state-sponsored actor. Some examples may not be reflected in the CFR database.
China
China likely possesses the second most sophisticated cyber capabilities in the world, which it leverages to achieve its policy objectives. Chinese state-sponsored cyber activities have been mainly in the forms of cyber espionage operations to steal intellectual property and trade secrets from corporations in order to acquire Western technology, operations to censor content considered “politically sensitive” and damaging to the Chinese Communist Party’s legitimacy, and disinformation campaigns as seen during Taiwan’s 2019 elections.
Cyber Incident
- Year: 2017
- Type of attack: Distributed Denial-of-Service (DDoS)
- Perpetrator: China
- Target: Google
- Cost: DDoS attacks cost on average $2 million for enterprise businesses and $120,000 for small to medium-sized businesses (SMBs).
- Impact: Google suffered the largest DDoS attack on recorded, in which traffic on its networks peaked at 2.5 terabits per second (tbps). While the company was able to mitigate the attack, the incident emphasized the need to address cybersecurity internationally. More than four billion people use Google for search and more than 1.5 billion people use Gmail. Major companies, such as Airbus, Citigroup, Deutsche Bank, Goldman Sachs, PayPal and UPS, rely on Google Cloud, and a DDoS attack could disrupt the financial and logistics industries, among others.
Russia
To achieve recognition in claimed spheres of influence, Russian cyber activities work to constrain and undermine democratic governments and ideals. According to the Harvard Belfer Center’s 2020 National Cyber Power Index, Russia ranks fourth in terms of its cyber capabilities, following the United States, China and the United Kingdom. Russian disinformation campaigns seek to erode public trust in Western democratic processes and “sow divisiveness” among citizens. The Russian government has also regularly conducted cyber operations against European and US critical infrastructure.
Cyber Incident
- Year: 2020
- Type of attack: Supply chain attack
- Perpetrator: Russia
- Targets: SolarWinds, other private companies, and the US federal government
- Cost: $25 million in damages, $90 million in estimated insured losses
- Impact: The attack on SolarWinds is considered one of the largest and most sophisticated cyberattacks ever perpetrated from a technical standpoint. The operation may have affected an estimated 18,000 SolarWinds Orion IT management software customers. It targeted seven federal agencies in the US and private companies in Belgium, Canada, Israel, Mexico, Spain, the UAE, the UK and the United States. The hackers may have sought to obtain emails of corporate executives and files about sensitive technologies under development, and information on US government activities.
Iran
Iranian cyber operations are motivated by the regime’s desire to project regional power and to challenge historical opponents such as Israel, the UK and the United States. The country’s cyber capabilities typically focus on the surveillance of political opponents, attacks on critical infrastructure within Western countries (as seen with its attempted hack of a New York dam in 2013), and IP theft from commercial entities and universities in support of its key industries, such as defense, telecommunications, natural resources, and energy, among others.
Cyber Incident
- Years: 2013–2017
- Type of attack: Cyber espionage
- Perpetrator: Iran
- Targets: Universities, businesses, government agencies and international organizations
- Cost: $3.4 billion
- Impact: The coordinated cyber intrusion campaign affected computer systems of almost 8,000 professors at 320 universities around the world. The targets also included the United Nations, 30 US companies and five US government agencies. The hackers stole 31.5 terabytes of documents and data. In 2018, the US Department of Justice indicted nine hackers located in Iran for orchestrating the attack, but the suspects have not been extradited to the US because the two countries do not have diplomatic relations.
North Korea
Although North Korea has one of the smallest internet presences in the world, with the majority of its Internet access routed through China, its government has dedicated resources to develop its cyber capabilities. According to the Center for New American Security (CNAS), most North Korean cyber operations center on espionage, theft, website vandalism, denial-of-service attacks and ransomware in an effort to circumvent financial sanctions and acquire the research and funds to pursue the country’s foreign policy objectives, particularly the development of its nuclear weapons program.
Cyber Incident
- Years: 2017–2018
- Type of attack: Ransomware
- Perpetrator: North Korea
- Targets: Windows XP computers
- Cost: $4 billion to $8 billion
- Impact: Using a leaked National Security Agency (NSA) exploit called EternalBlue, the attack encrypted user data and demanded payment in bitcoin to regain access. The incursion affected 200,000 computers across 150 countries. The attack on the UK’s National Health Service (NHS) cost an estimated £92 million ($100 million) and cancelled more than 19,000 appointments. In 2018, a new variant of WannaCry spread to 10,000 machines in Taiwan Semiconductor Manufacturing Company’s (TSMC) most advanced facilities, forcing TSMC to temporarily shut down several of its chip-fabrication factories. The disruption affected the company’s financial performance, resulting in a $170 million in losses.
United States
By most estimates, the United States possesses the most advanced cyber capabilities of any nation. Described as the both the “hunted and hunter,” US strategy in cyberspace is grounded in “proactive defense,” in which hacking is done preemptively to deter potential attacks. Recently, the US government has struggled to retain top cyber professionals, with some former US government hackers accepting jobs with foreign governments and working for firms such as the UAE-based group DarkMatter, which has allegedly targeted Americans for surveillance.
Cyber Incident
- Years: 2011–2016
- Type of attack: Cyber espionage
- Suspected Perpetrator: United States
- Targets: Organizations across various industries and governments
- Cost: Unknown
- Impact: A group called Strider or Project Sauron has been conducting long-term cyber espionage operations against 30 organizations from the government, military, finance, telecommunications and scientific research sectors in Belgium, China, Iran, Russia, Rwanda and Sweden, among others. Given the level of sophistication of Strider’s operations and the vast resources needed to sustain these cyber activities, analysts believe that the group is state-sponsored, and according to CFR’s Cyber Operations Tracker, it is suspected to be sponsored by the United States. The group was last known to be active in 2016. While these operations have largely ceased, the group may still be active on computer systems.
Direct and Indirect Costs of State-Sponsored Attacks are Mounting
In addition to the harm inflicted on the direct targets, cyber vulnerabilities pose serious risks to the global economy as hacks cause large-scale business disruptions, revenue loss and reputation damage. For example, the 2017 NotPetya attack targeted Ukraine, but the impacts spread across Australia, Europe, and the United States, devastating global businesses and critical infrastructure and causing an estimated $10 billion in losses. According to the Foundation for Defense of Democracies, a three-day cyber disruption of a managed service provider can lead to an economic loss of almost $80 billion. The hidden consequences of cyberattacks include insurance premium increases, higher interest rates for borrowed capital if a potentially vulnerable entity is perceived as a high-risk borrower, loss of contract and future opportunity revenue, and loss of trust by customers and citizens.
While intangible losses are difficult to quantify, they play a significant role in the decision-making and risk assessments of potential targets. Often, in fear of reputational costs, companies overstate their confidence in their ability to address cyber threats, particularly those posed by states actors, with firms in Asia exhibiting greater concern and readiness than their European or North American counterparts. Indeed, a Ponemon study determined that 47 percent of private-sector organizations in the UK and the US have not assessed the readiness of their incident response teams. A 2020 review by Dragos also found that 90 percent of analyzed companies had little to no visibility into their industrial control system (ICS) environments, which play essential roles in critical infrastructure management and security. Given that in the US, 85 percent of federal infrastructure is owned by the private sector, according to the US Federal Emergency Management Agency (FEMA), these assessments suggest that government defenses are likely not faring much better.
Global Risks and Estimated Costs of Cyberattacks on Power Plants
Energy infrastructure, including power plants, is critical for the health, welfare, safety and economies of countries. Cybersecurity risks to critical power infrastructure are growing. A 2019 Siemens and Ponemon Institute study found that 56 percent of companies surveyed suffer at least one shutdown or loss of operational data per year. The following graphic illustrates the potential impact that a cyberattack on a country’s power plants could have on its power supply and its citizens.
Power substations present a particular cybersecurity vulnerability to countries’ electrical grids. A 2014 study by the US Federal Energy Regulatory Commission (FERC) found that if a cyberattack were to occur on nine strategic substations, it would cause a coast-to-coast electrical grid shutdown.
Note: The following countries were chosen according to their total primary energy consumption as of 2017. Because of limitations in publicly available data, 2017 is the most current information available on electricity generation, population total, share of the population’s access to electricity and estimated power plant generation. To calculate the percentage of a country’s electrical output that would be disrupted by a cyberattack on a power plant, the estimated electricity generation of the largest power plant in the country or the sum of the estimated generation of the top 10 power plants are compared with the total electricity generation of that country. Based on that calculation, the potential number of individuals who have access to electricity in each country that could be affected is determined. The loss of power in a country would affect both citizens and industries. This analysis estimates the impact that a successful cyberattack could have on the share of individuals in that country who have access to electricity.
Click buttons below to see potential affects of power plant attacks
Country | Percent of population | Number of people potentially affected
Country | Percent of population | Number of people potentially affected
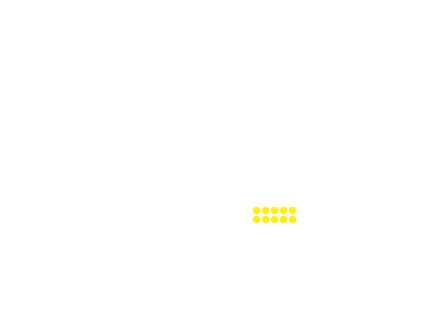
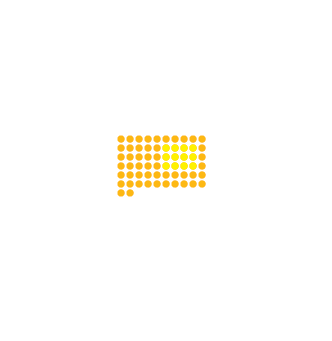
China | 1.32% | 18,737,352

United States | 0.52% | 1,680,044
An analysis of a hypothetical scenario by Lloyd’s and the University of Cambridge of a cyberattack on the US electrical grid servicing New York City and Washington, DC, estimated an economic impact of up to $1 trillion in addition to the intangible costs of unrest, industrial accidents, and insurance implications
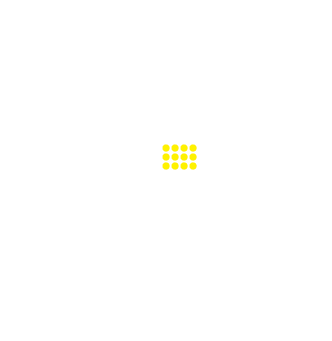
Russia | 3.76% | 5,470,575
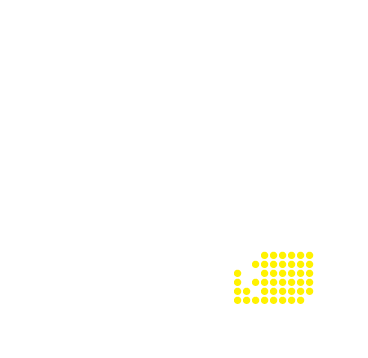
India | 2.36% | 29,272,675

Japan | 6.63% | 8,451,243
An analysis of 15 countries by the International Institute for Strategic Studies found that Japan, despite its reputation as a leader in information and communication, is less capable in cybersecurity and ranks in the lowest tier alongside India, Indonesia, Iran, Malaysia, North Korea and Vietnam. Despite being known as a leader in information and communication technologies, the International Institute for Strategic Studies found that in a study of 15 countries, Japan is less capable in cybersecurity and ranks in the lowest tier alongside India, Indonesia, Iran, Malaysia, North Korea, and Vietnam.
Canada | 5.07% | 1,851,846
Germany | 3.81% | 3,153,418

Brazil | 0.07% | 145,619
Brazil’s assessment includes its top 12 power plants, as there are no estimates of power generation for two of its top 10 power plants.
South Korea | 7.07% | 3,609,628
North Korean-backed actors are increasingly targeting the South Korean government and national infrastructure, with South Korean government sources stating that on average, 1.5 million cyberattacks were launched each day against the public sector in 2020. In pursuit of its nuclear ambitions, state-sponsored actors from North Korea have particularly targeted South Korea’s nuclear energy sector, such as nuclear power plant operators.
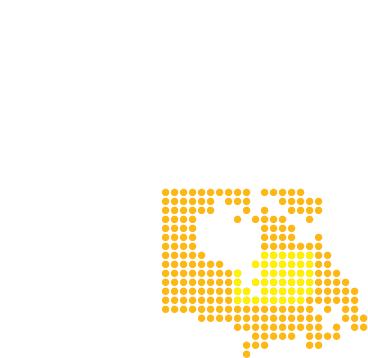
Iran | 5.14% | 4,140,992
Damavand C.C. possess the largest electricity capacity (MW) in the world, according to the Global Power Plant Database.
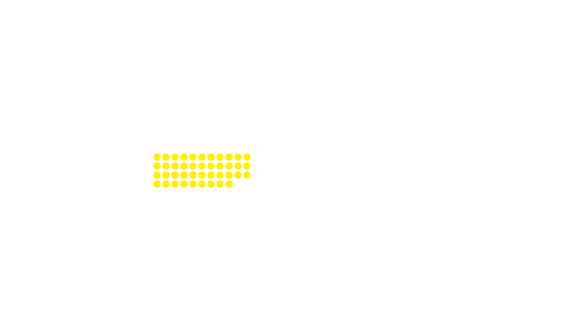
China | 5.8% | 82,879,502

United States | 4.8% | 15,708,294
An analysis of a hypothetical scenario by Lloyd’s and the University of Cambridge of a cyberattack on the US electrical grid servicing New York City and Washington, DC, estimated an economic impact of up to $1 trillion in addition to the intangible costs of unrest, industrial accidents, and insurance implications
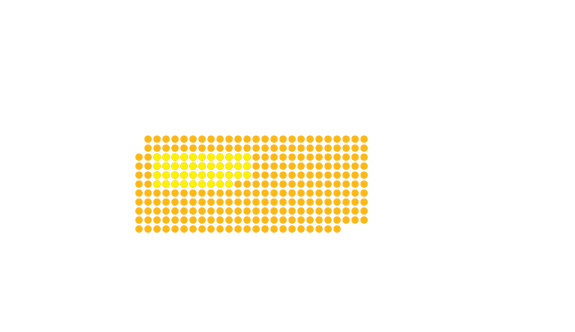
Russia | 24.9% | 36,217,085
India | 12.5% | 154,444,313
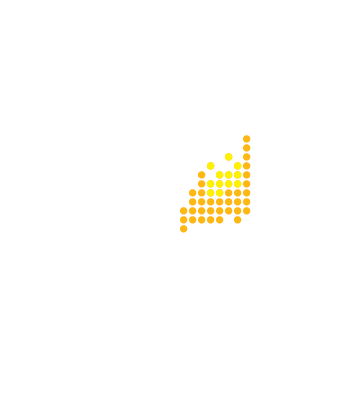
Japan | 25.6% | 32,586,836
An analysis of 15 countries by the International Institute for Strategic Studies found that Japan, despite its reputation as a leader in information and communication, is less capable in cybersecurity and ranks in the lowest tier alongside India, Indonesia, Iran, Malaysia, North Korea and Vietnam. Despite being known as a leader in information and communication technologies, the International Institute for Strategic Studies found that in a study of 15 countries, Japan is less capable in cybersecurity and ranks in the lowest tier alongside India, Indonesia, Iran, Malaysia, North Korea, and Vietnam.
Canada | 29% | 10,602,005
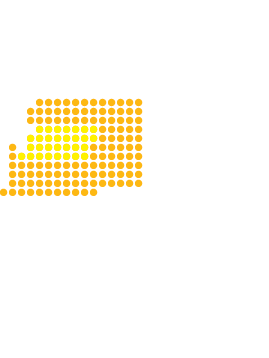
Germany | 18.5% | 15,303,232

Brazil | 0.1% | 176,510
Brazil’s assessment includes its top 12 power plants, as there are no estimates of power generation for two of its top 10 power plants.
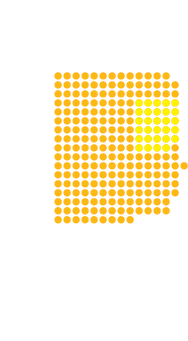
South Korea | 56.6% | 28,900,082
North Korean-backed actors are increasingly targeting the South Korean government and national infrastructure, with South Korean government sources stating that on average, 1.5 million cyberattacks were launched each day against the public sector in 2020. In pursuit of its nuclear ambitions, state-sponsored actors from North Korea have particularly targeted South Korea’s nuclear energy sector, such as nuclear power plant operators.
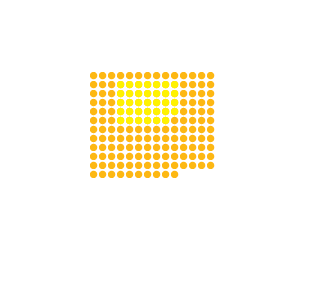
Iran | 25% | 19,976,549
Damavand C.C. possess the largest electricity capacity (MW) in the world, according to the Global Power Plant Database.
SOURCES: U.S. Energy Information Administration. (n.d.). International. Retrieved July 13, 2021, from https://www.eia.gov/international/overview/world, World Resources Institute. (2021, June). Global Power Plant Database Data. Retrieved from https://datasets.wri.org/dataset/globalpowerplantdatabase, and the World Bank. (n.d.). Access to electricity (% of population). Data. Retrieved July 13, 2021, from https://data.worldbank.org/indicator/EG.ELC.ACCS.ZS?end=2017&most_recent_year_desc=true&start=2013
Current Cybersecurity Responses Are Insufficient to Deter Cyberattacks
There is no clear consensus regarding who is liable for cybersecurity breaches, what constitutes an act of war or how to impose penalties for specific cyber intrusions. Governments have used various “seen and unseen” responses, including sanctions, offensive cyber operations and kinetic attacks, such as Israel’s air strike on the Hamas Cyber Headquarters building in response to an cyberattack by the Palestinian organization in 2019. Since 2012, the US Treasury Department has issued 311 cyber-related sanctions—the greatest number against Russia, Iran and North Korea—and in 2020, the EU for the first-time imposed sanctions against individuals and entities from China, North Korea and Russia in response to foreign cyberattacks. However, continued hostile state-sponsored cyber activity suggests that these tactics have not been effective deterrents.
Although sanctions can potentially deter state-sponsored cyberattacks, evidence suggests that state and non-state actors have not been compelled to follow standard rules of behavior or relinquish their cyber capabilities. Malicious actors that seek to achieve short-term goals may not experience the medium- to long-term impacts of sanctions, thus hindering their utility and effectiveness as a deterrent. The efficacy of sanctions is further weakened by uneven enforcement in regions with poor sanctions compliance and legal frameworks, such as Southeast Asia, and countries with policies and governance structures that may mask suspected perpetrators’ identities. In some cases, governments may also refuse to extradite accused perpetrators when indicted for a cyberattack in another nation. These conditions cultivate an environment in which state and non-state actors have limited risk of prosecution.
To date, governments have largely attempted to combat cyber intruders independently, but given the millions of attempted cyberattacks occurring daily, it is extremely difficult for individual governments to effectively respond to all multi-faceted attacks.
In 2020 study by Deep Instinct, malware and ransomware attacks increased by 358 percent and 435 percent, respectively, as compared with 2019.
Adding yet another dimension of complexity, experts note that threat actors, particularly those that are state-sponsored, are adapting to more robust security in the critical infrastructure sector by looking for vulnerabilities among IT organizations, non-government organizations (NGOs), commercial facilities, critical manufacturing, financial services and the defense industrial base. These challenges, among others, require the cooperation among countries, the private sector and civil society, and the establishment of rules of behavior to protect the international community’s collective cybersecurity.
Greater Multistakeholder International Collaboration on Cybersecurity Is Needed
The private sector, governments and international organizations have put forth a number of frameworks and recommendations for international norms, including the March 2021 consensus report from the UN open-ended working group on developments in the field of information and telecommunications in the context of international security; a Russia-led proposed UN resolution on cybercrime; a UNGGE 2021 report on advancing responsible state behavior in cyberspace in the context of international security; the Global Commission on the Stability of Cyberspace; the Charter of Trust; and the Cybersecurity Tech Accord, among others. The Paris Call for Trust and Security in Cyberspace—with more than 1,200 endorsers, the largest multi-stakeholder group ever assembled in support of a cybersecurity-focused agreement—attempts to provide a baseline for continuing cyber norms discussions and enables meaningful cooperation among countries, civil society and the private sector, but it notably does not include China, Russia, or the US.
However, as the cyber arms race has escalated, these initiatives remain disparate with a lack of consensus on which international norms to follow. Critics point out that cyberattack motives are difficult to define, and that determining hackers’ identities can be difficult (although not impossible). More fundamentally, governments are reluctant to relinquish their cyber capabilities as tools of effective statecraft because they do not want to limit their own freedom to launch cyberattacks on adversaries. As a result, countries fail to follow voluntary norms on what is permissible in cyberspace. Absent effective governance and regulation, the private sector has established its own self-regulating mechanisms and standards of behavior, but they are insufficient as cyber activities escalate and impact all stakeholders in the digital ecosystem. The challenge for the international community will be to secure an agreement that establishes clear rules and enforcement mechanisms that would be acceptable to most countries while also addressing all attack vectors within the cyber domain, including mis/disinformation, theft of intelligence and IP, and critical infrastructure security. Such an agreement is sorely needed and would help to strengthen security in the global digital ecosystem. As digital connectivity proliferates, so does the global attack surface, underscoring the urgency to establish new norms of responsible behavior in cyberspace to mitigate the mounting costs of cyberattacks and risks to human security.

